Using a Classroom-Based Deese Roediger McDermott Paradigm to Assess the Effects of Imagery on False Memories
Summary
The method presented here induced false memories using lists of related words and also assessed the effects of imagery instructions on the recall and recognition of those false memories. This protocol details a modified version of the Deese Roediger McDermott (DRM) paradigm.
Abstract
Associated word list procedures can elicit false memories in predictable ways by inducing associative processing, thus making it harder to monitor the accuracy of memories. The purpose of the method presented here was to induce false memories using lists of either semantically or phonologically related words and to assess the effects of imagery instructions on the recall and recognition of those false memories. To do this, we used a modified version of the Deese Roediger McDermott (DRM) paradigm. We adapted word lists from previous DRM studies to suit imagery procedures and created an automated presentation to present the word lists in classroom settings. We then recruited undergraduate classes and instructed some of the classes to create mental images of the list words as they were being presented, while instructing the other classes to simply remember the words. The automated presentation presented word lists to participants, one word at a time, alternating between phonologically and semantically related lists. Participants used paper-pencil recall packets to immediately recall list items, complete a distractor activity, and take a subsequent final recognition test. Often, participants immediately recalled and later recognized words that were related to the list items but were not actually presented; these are known as critical lures and indicate a false memory. The protocol detailed here describes a four-step procedure – list presentation, immediate recall, distractor phase, and final recognition – that can assess the effects of list type and imagery instruction within the DRM paradigm on memory. The automated nature of the list presentation provides the ability to systematically vary variables of interest, and the paper and pencil method of data collection affords an easily accessible method for collecting data in classroom settings. The protocol also offers options to modify the procedure to a more traditional DRM paradigm without imagery and/or list type manipulations. The use of this protocol can provide results relevant to both classroom learning and cognitive science principles.
Introduction
Memory is malleable and fallible, and these days people realize the limitations of their own memory system. But how do memory errors arise? What mechanisms are responsible for errors in memory retrieval? We modified a widely used and highly cited laboratory-based procedure called the Deese Roediger McDermott paradigm (DRM)1,2 to investigate the influence of different variables on memory errors. In traditional DRM procedures, participants are asked to learn lists of semantically related words (e.g., table, couch, desk, lamp, pillow, stool, bench, rocker). When later asked to recall and/or recognize the words from the lists, participants often report seeing words that were semantically related to the lists but not actually studied (e.g., chair). False memories for these words, referred to as critical lures, can occur 55% – 80% of the time in standard procedures2,3.
The Activation Monitoring Framework is often cited as a theoretical basis for memory errors that arise from the DRM paradigm. Specifically, DRM false memories are attributed to the dual processes of activation (i.e., the tendency for pieces of information currently active in working memory to "spread" and also activate other, related pieces of information) and monitoring (i.e., assessing the accuracy and/or source of something being remembered)5,6. The process of studying semantically related DRM lists causes activation to spread from the list words to the critical lure and thus activates the critical lure in working memory. The result is a false memory that may not be accurately monitored during later tasks.
The three-phase testing procedure inherent to the DRM paradigm allows cognitive psychologists to manipulate a number of variables during the process of encoding (study of the list items), retention (storage of the list items while completing a distractor task to disrupt working memory), or retrieval (a memory test), to better understand the specific processes that contribute to memory errors. Our procedure expands use of traditional DRM procedures to directly compare memory error rates for different types of content during encoding (e.g., semantically related versus phonologically related)9, test type during retrieval (e.g., a recall task versus a recognition task)10 and, perhaps most notably, imagery encoding processes during list study11,12,13,14.
Our primary interest in developing this protocol was to better understand possible effects of imagery on recall and recognition, particularly whether the effects of creating mental images of the list words during encoding (e.g., imagining them) would vary according to whether the list words were related to the critical lure according to sound (i.e., phonologically) or meaning (i.e., semantically). For instance, for the phonological list log, hog, dock, bog, fog, doll, frog, jog, and dot, the critical lure is dog. For the semantic list mug, saucer, tea, coaster, lid, coffee, straw, and soup, the critical lure is cup. We were interested in whether imaging the list words affected the associative processing for those lists differently. While traditional DRM word lists contain 12-15 semantically related list words2, our procedure employed 8-item word lists. These lists were modified from 16-item lists previously developed to investigate the converging effects of phonological and semantic word associations on false memories9. In order to adapt typical DRM procedures to include imagery instructions, we shortened the word lists by selecting the 8 words from each list that were easiest to create mental images of. This allowed for the elimination of less concrete words (e.g., pun, worst) that were hard to imagine. Additionally, we modified a computer-based word list presentation utilized in previous research15 to standardize the presentation of materials and also developed paper/pencil recall and recognition measures to more appropriately suit classroom environments.
Our results did not suggest an interaction between list association type and imagery procedures, but they did demonstrate the significant main effects of imagery and list type14. We pursued this line of inquiry because of the robust literature of imagination inflation effects suggesting enhanced feelings of belief and memory in past childhood events that are repeatedly imagined16,17,18. However, recently researchers suggest that perhaps not all imagery is created equal and that the nature of imagery instructions mediates the effects on false memory rates19. One possible limitation to the work assessing imagination inflation effects is inherent in the procedure itself. That is, participants are asked to provide Likert scale ratings of their confidence or belief in experiencing certain events in childhood, and following imagination of those events, ratings are provided a second time to assess changes (specifically increases) in those ratings. One possible problem with this procedure is a lack of control over the veracity of experiences that participants must identify with confidence ratings both prior to and after the imagery phase. In some studies, researchers consult family members for corroboration20; however, a majority of the research examining imagination inflation relies solely on the word of the participant.
DRM procedures offer methodological advantages over other memory paradigms, including imagination inflation procedures, because researchers maintain control over the content being activated in working memory through the design of the lists. Specifically, researchers select the list items according to their associative strength to the critical lure and can easily measure when a participant commits the targeted memory error (e.g., chair was not on the studied list but was recalled at test). This content control provides insight into processes that drive associative memory errors, affording researchers the opportunity to explore other potentially important factors driving false memory errors, such as the construction of visual images during list encoding21 or even elaborating on the list items to generate complex event narratives11.
This protocol employs a presentation administration of materials and a paper and pencil format of data collection that allows researchers to collect participant data in large groups (e.g., classrooms), while systematically varying variables. The accessibility and experimental control offered by this protocol provides an opportunity to teach students about memory processes with an in-class demonstration while reliably collecting data. Compared to laboratory-based DRM procedures, this context makes results more applicable to classroom learning, thus informing both cognitive science and educational psychology. In addition, this protocol provides optional modifications that can be utilized to remove the usage of imagery instructions or varying list types, thereby offering a construction-kit type approach that allows for more personalized use.
Protocol
All methods described here have been approved by the Institutional Review Board of Georgia State University.
1. Material Preparation
- Using the word lists attached in the supplemental materials, create four separate presentations: Imagery A, Imagery B, Non-imagery A, and Non-imagery B. Ensure that all four presentations are void of templates or designs, with white backgrounds and black font. The two list orders, A and B, serve to balance any effects of list order or fatigue. The two imagery versions serve to assess the effects of imagery instructions on memory.
- Begin each presentation with a content slide titled, "Instructions". In the body of the instructions slide, include the relevant instructions listed below in 24+ point font according to whether the presentation is designated as imagery or non-imagery.
- Include these instructions for Imagery A and Imagery B presentations: "I will present words from a list, one at a time, on the projector. As each word is presented, please create a mental image of that word in your mind. Please do not mark on the packet while the list is being presented. When each list is finished, the projector will indicate, "RECALL", and you will write down the words you remember from the list in the packet provided. Try to use the images you created to help you recall the words. After you have written down all the words that you can remember, please indicate overall how easy it was for you to create mental images for that list. You will be given 45 seconds to recall the list and rate the ease of creating images, and then we will move on to the next list. When we do so, please flip to the next page in the packet. It is important that you do not revisit any old lists once we have moved on. There will be 11 lists in total, the first being a practice list. After all the lists have been presented, you will be asked to complete a word search task."
- Include these instructions for Non-imagery A and Non-imagery B presentations: "I will present words from a list, one at a time, on the projector. Pay attention to the words on the projector. Please do not mark on your packet as the words are being presented. When each list is finished, the projector will indicate "RECALL", and you will write down the words you remember from the list in the packet provided. You will be given 45 seconds to recall as many words from the list as you can, then we will move on to the next list. When we do so, please flip to the next page in the packet. It is important that you do not revisit any old lists once we have moved on. There will be 11 lists in total, the first being a practice list. After all the lists have been presented, you will be asked to complete a word search task."
- Following the instructional slide, create timed slides to present lists and prompt recall. All text is center-aligned. List words are 72 point font, and all instructional cues are 44 pt. font.
- Create slide 2 and include the text "Prepare for the practice list" centered vertically and horizontally on the slide in 44 point font.
- On slides 3-10, present the practice list words in order, one word per slide, centered horizontally and vertically, in lower case font. Designate a slide duration of 5 seconds by going under Transitions in the menu and selecting to advance the slide after 00:05.00.
- On slide 11, indicate the end of the practice list and the beginning of recall. Include "End of Practice List" in black font with "RECALL" double-spaced below it in red font. Designate a slide duration of 45 seconds.
- After the practice list recall slide, create slides to present the test lists in the same manner.
NOTE: The procedure for each list is 10 slides long. The first slide indicates "Prepare for List X". The following 8 slides include the list words in order, each on a separate slide with 5 second durations. Following the list word slides, a recall slide with a designated duration of 45 seconds indicates "End of List X" in black font with "RECALL" double-spaced beneath it in red font. Adapt the "X" in the "End of List X" text to indicate the order of the lists in that particular presentation, not the order of the lists as they are listed in the appendix. For example, the 3rd list to occur in the presentation will read "End of List 3". - Ensure that the order of the lists in the slides varies according to the particular presentation . According to the numbered designations in the word lists attached to the supplemental materials, Imagery A and Non-Imagery A presentations present lists in ascending order: practice, 1, 2, 3, 4, 5, 6, 7, 8, 9, 10. Imagery B and Non-imagery B presentations present lists in descending order: practice, 10, 9, 8, 7, 6, 5, 4, 3, 2, 1.
- After the recall slide for the last list, ensure that slide 112 includes the following text "End of word lists. Turn to the next page in your packets and please take the next 7 minutes to work on the attached word searches." Designate a slide duration of 7 minutes.
- Create slide 113 to include "End of word searching. One last activity". This slide has no designated duration. Create a final slide, 114, that includes a thank you.
- Begin each presentation with a content slide titled, "Instructions". In the body of the instructions slide, include the relevant instructions listed below in 24+ point font according to whether the presentation is designated as imagery or non-imagery.
- Create two different versions of recall packets, imagery and non-imagery, in a word processor. Page 1 of both versions prompts participants to write down their name, gender, age, major, or any other demographic variables of interest. Page 13 of both versions includes a word search with dimensions of 20 x 20 letters or larger. Ensure that no list or practice words occur in the word search.
- Ensure that pages 2-12 in the recall packets include repeated recall activity pages, which vary according to the version.
- Ensure that recall activity pages for the imagery version include the following instructions at the top of the page: "Instructions: Create an image of each item in your head. Use the images you created to help you recall the words." Below that, the activity page includes "Recall:" with at least ⅓ of the page following it left blank. At the bottom of the page, include the following prompt: "Overall, how easily did these images come to mind for this list? Circle one". Below the ease of imagery prompt, include the following options for participants to circle: "0 – Not easy, 1 – Somewhat easy, 2 – Very easy".
- Ensure that recall activity pages for the non-imagery version include the following instructions at the top of the page: "Instructions: Please recall and write down all the words you remember from the current list." Below that, the page indicates "Recall:" with no other prompts following.
- Obtain the final recognition test from the supplementary materials and do not attach it to the recall packets. It is an individual page to be handed out separately. The final recognition test consists of 80 items total.
- Of the 80 items, use 30 from the lists presented on the presentation slides at the start of the study. The 30 presented items chosen for the recognition memory test are the 1st, 3rd and 7th words from each of the 10 lists presented (15 semantic items and 15 phonological items).
- Include each of the 10 critical lures related to the 10 presented lists (5 semantic and 5 phonological) on the test.
- For the additional 40 items, use the DRM lists not presented to participants, including the 1st, 3rd and 7th items from each of 10 non-presented lists (15 semantic and 15 phonological items), as well as the associated critical lure (5 semantic and 5 phonological) for each of the 10 non-presented lists. The non-presented lists are located along with the presented lists in supplementary materials.
- Arrange the items on the recognition memory test such that one item from each of the 10 presented lists and 10 non-presented lists appears prior to any critical lures. List items are not thematically blocked on the memory test.
- Ensure that instructions on the recognition test prompt participants to indicate "yes" or "no" in writing as to whether each item appeared in any of the lists presented.
2. Recruitment
- Recruit at least four face-to-face sections of the same, or very similar, undergraduate class. If possible, recruit non-psychology classes or introductory courses that have not learned about false memory paradigms.
- Include all students who are enrolled in the recruited classes and have normal or corrected vision to participate.
- Assign each class section to 1 of the 4 presentation types, distributing the number of classes assigned to each presentation type as evenly as possible and prioritizing even distribution across imagery and non-imagery presentation types.
3. Optional Modifications to Protocol
- If the effects of imagery instructions are not of interest, modify the protocol as follows to only include one set of instructions, one type of recall packet, and shorter slide durations.
- Using the word lists attached in supplemental materials, create 2 separate presentations, versions A and B. Present the 10 study lists in ascending order following the practice list in the version A presentation (practice, 1, 2, 3, 4…), and present the lists in descending order following the practice list in the version B presentation (practice, 10, 9, 8, 7…).
- Include the non-imagery instructions from protocol item 1.1.1.2 on the first slide of both presentation versions.
- Modify the timed list presentation slides described in 1.1.2.2 to be 2 seconds long instead of 5 seconds. In other words, design the presentation so that each word is presented to participants for 2 seconds. Do not modify any other types of timed slides, like the recall slides (45 seconds) or word search side (7 minutes).
- Create 1 version of the recall packet (i.e., non-imagery version) that includes the traditional non-imagery instructions from protocol item 1.2.3.
- Assign the recruited classes to the 2 presentation types as evenly as possible.
- If the effects of list type (semantic vs. phonological) are not of interest, modify the protocol as follows to only include longer, traditional semantic DRM lists:
- Do not use the word lists included in our supplementary materials, with the exception of the practice list. Instead, select 20 of the unmodified DRM lists included in the original Roediger & McDermott study2. These word lists are 15-items long and all semantically related. Number the selected lists 1-20. Use lists 1-10 as study lists in the presentation and lists 11-20 as filler lists for the recognition test.
- Modify the presentations to accommodate 15-item lists instead of 8-item lists. Following the instruction slide and practice list, the procedure for each test list is 17 slides long. For each list, the first slide indicates "Prepare for List X", the following 15 slides present the list words one at a time, and the last slide for the list indicates the end of the list and the beginning of recall.
- Modify the recognition test design described in 1.3 to include the 1st, 8th, and 10th words from the 10 study lists and 10 filler lists and their critical lures.
4. Procedure
- At the beginning of a regularly scheduled class session, ask the instructor to leave the room and pull up the presentation that was assigned to that class section.
- Introduce yourself as the researcher and distribute informed consent forms to students. Allow students to read through the informed consent document on their own. Prompt them to complete the informed consent form and to ask any questions about the document or participation.
- Distribute the appropriate recall packets to participants. If using an imagery condition, ensure that classes who were assigned one of the two imagery presentations receive an imagery recall packet. Do not distribute the recognition test yet.
- Instruct participants to fill out the initial page of the recall packet with demographic information. Then read the instructions from the presentation aloud with the slide presented.
- Instruct participants to flip to the next page in their packet for the practice list, move to presentation slide 3 (i.e., "Prepare for the practice list"), and read the prompt aloud. After reading the prompt, move to slide 4 and allow the presentation to progress through the timed practice list slides.
- When the practice list recall slide expires and automatically moves to the next list prompt slide (i.e., "Prepare for list 1"), prompt participants to ask any questions they have about the procedure. Answer any questions and instruct participants to turn to the next page (pg. 3) in their packet for list 1.
- Once all participants have turned to the next page in their booklet, read the list 1 prompt slide aloud (i.e., "Prepare for list 1") and progress to the timed list 1 word list and recall slides.
- Continue this procedure for the 9 remaining lists, prompting participants to flip to the next page in their booklet after each recall slide expires, reading the "prepare for list X" slide aloud, and subsequently prompting the timed list slides.
- After recall for list 10, supervise as the presentation prompts participants to turn to the next page in their packet and work on the word search for 7 minutes.
- When the presentation automatically progresses to the final slide (i.e., "One last activity"), collect the recall packets from participants and distribute the final recognition test.
- Instruct participants to complete the final recognition test at their own pace and to do their best not to leave any items blank. Once all participants have finished the test, collect the recognition tests and verbally debrief participants (see supplementary materials for debriefing statement).
Representative Results
Effects of DRM Procedures on False Memories: Standard DRM Instructions without Imagery
To illustrate standard DRM procedures' ability to induce false memories, we analyzed rates of falsely remembering non-list words during recall and recognition. Table 1 reports proportions for the different types of false remembering that occurred during recall and recognition. During immediate recall, participants recalled unpresented words on 20% of the lists, suggesting the protocol induced spreading activation to unpresented words that were then immediately remembered as being seen on 1 out of every 5 lists. Of those false recalls, 13% were recalls of the critical lures and 8% were recalls of other non-list words, which we refer to as non-critical lures. A repeated measures analyses comparing the proportion of lists in which the critical lure was recalled and the proportion of lists in which a non-critical lure was recalled indicated that participants recalled critical lures at significantly higher rates than non-critical lures, F(1, 48) = 9.24, p = .004. While this finding suggests that the DRM protocol successfully converged on and activated the critical lures more so than other words, it was not to the degree that longer DRM lists typically do. For instance, the longer 15-item lists described in protocol modification 3.2 can induce recall of the critical lure up to 55% of the time2.
To measure the effects of DRM procedures on the recognition of critical lures during the final recognition test, we compared the proportion of critical lures remembered (number of "yes" recognitions/10) to the proportion of non-critical lures remembered, which included filler list words used as distractors and their critical lures (number of "yes" recognitions/40). Repeated measures comparisons of these proportions indicated that critical lures were recognized at significantly higher rates than non-critical lures, F (1, 48) = 149.52, p < .001. Critical lures were recognized 45% of the time, whereas distractor words were only recognized 6% of the time, illustrating that the protocol induced high rates of false critical lure recognition.
When directly comparing rates of false memories across recall and recognition, a repeated measures analysis indicated that significantly higher proportions of critical lures were remembered during the recognition test (45%) than during immediate recall (13%), F (1, 48) = 145.14, p < .001. This finding is typical and demonstrates the different demands that each task places on memory and also illustrates the ability of this protocol, which utilized both types of memory tasks, to capture instances of false memory that were present during one task but not the other. The final recognition task measured instances of false memory that were absent during free recall.
To compare the effects of using phonologically-related versus semantically-related DRM lists on false memories, we calculated separate proportions of critical lure recall and critical lure recognition for each list type (number recalled or recognized/5). See Table 1 for proportions of false memories across list types. A 2 (test type: recall vs. recognition) x 2 (list type: semantic vs. phonological) mixed ANOVA indicated that critical lures for phonological lists were recalled at higher rates than critical lures for semantic lists (rates of 14% and 6%, respectively); whereas critical lures for semantic lists were later recognized at higher rates than critical lures for phonological lists (rates of 48% and 28%, respectively). This was evidenced by a significant interaction between list type and test type for false memories, F(1, 100) = 55.36, p < .001. This finding demonstrates that the type of association between the list words affects the type and/or level of processing induced during study (i.e., differences in recall performance) and later remembering (i.e., differences in recognition performance). Semantic lists induce deeper processing of the list association and critical lure, which makes reactivation of that critical lure particularly difficult to monitor during recognition; whereas phonological lists induce shallow associative processing that is confusing and hard to monitor during recall but that largely decays by the final recognition test.
Effects of Imagery Instructions during DRM Procedures
To demonstrate the effects of modified DRM procedures that instruct participants to create mental images of the list words, we compared hit rates (e.g., correctly recalling a list word) and false memory rates across participants in imagery and non-imagery conditions. We calculated separate proportions for recall and recognition hit rates by dividing the total number of list words correctly recalled by 10 and the total number of "yes" responses to list words on the recognition test by 30. A 2 (imagery vs. non-imagery) x 2 (proportion of recall hits vs. proportion of recognition hits) mixed ANOVA indicated a significant main effect for imagery instructions. Participants in the imagery condition remembered more list words than participants in the non-imagery condition during both recall (64% vs. 60%) and recognition (93% vs. 88%), F(1, 100) = 5.90, p = .02. A similar 2 (imagery vs. non-imagery) x 2 (proportion of critical lures recalled vs. proportion of critical lures recognized) mixed ANOVA on false memory rates indicated another main effect for imagery instructions, F(1, 100) = 3.82, p = .05. Participants who imagined the list words remembered fewer critical lures than participants receiving standard DRM procedures during both recall (7% vs. 13%) and recognition (39% vs. 45%).
A larger mixed model with list type added in as an additional repeated measure factor did not indicate any significant interaction between list type and imagery; imagery affected memory for both list types similarly. However, it is important to note that when list type was added to the mixed model, the impact of imagery on false recognition was only marginally significant, F(1,100) = 3.46, p = .066. Previous work has also indicated null effects of imagery during false memory recognition10, suggesting that simple imagery instructions (i.e., create a mental image in your head) are not sufficient aid during monitoring when the critical lure is reactivated during recognition. The relative decreases in false recall and increases in list word recall and recognition reported here are in line with previous work employing imagery instructions in DRM procedures10,23. Further, the effects of imagery would likely be more pronounced if protocol modification 3.2 was implemented, which utilizes longer semantically-related lists10.
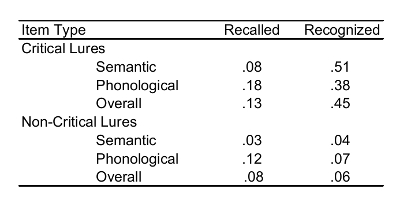
Table 1: Proportions of the Different Types of Words Falsely Remembered Following Standard Instructions. This table illustrates the proportions of the various types of words falsely remembered by the non-imagery group. Rates of false memories for critical lures and non-critical lures are illustrated across test type and list type.
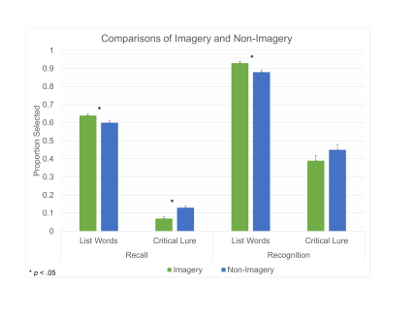
Figure 1: Comparisons of Imagery and Non-Imagery. This figure illustrates the proportions of list words accurately remembered and the proportions of critical lures falsely remembered during recall and recognition across imagery and non-imagery conditions. Error bars represent the standard errors. Please click here to view a larger version of this figure.
Discussion
The protocol employed in this study modified a widely used word list procedure, the Deese Roediger McDermott (DRM) paradigm, to assess the effects of associative processing with and without imagery instructions on false memories in a classroom-based procedure. The expansion to include the variables of list association type, test type, and imagery instruction implemented here afforded the ability to analyze how each of these complex factors influenced a learning context independently, as well as how they interacted, providing insight into memory processing strategies. This protocol also offers optional modifications that can be used if a more traditional DRM procedure is desired, wherein imagery instructions or different list types are employed. These modifications can be implemented by only using the non-imagery condition with shortened presentation durations and/or substituting longer semantically-related word lists.
The automated presentation of DRM materials described in this protocol affords absolute control of presentation duration, which is an essential element to control considering that the length of presentation duration impacts recall across phonological and semantic lists differently22. A relatively long 5-second presentation duration was employed here to allow time for participants to engage in imagery procedures. However, the presentation can be easily modified (see protocol 3.1) to utilize shorter presentation durations when imagery is not being used. Shorter durations are associated with increased false memory rates for both phonological and semantic lists22. This automated format also allows for systematic control of list order presentation, which is necessary for counterbalancing the presentation of both list types. The false memory rates for phonological and semantic lists reported here suggests that the protocol's alternating presentation of list types successfully induced the associative processing inherent to each list type, and the significant interaction between list type and test type reported here demonstrates that phonological and semantic associative processing apply different constraints on memory.
The simple imagery instructions employed here were sufficient to significantly increase memory for list words and decrease false memory recall, but were not sufficient to decrease false recognition after a distractor activity. Using imagery instructions in this context not only provides insight into the mechanisms responsible for associative processing and source monitoring during classroom learning, but also has the ability to demonstrate the usefulness of creating visual memory cues to students.
The word lists included in this protocol were modified from previously normed word lists9 to only include concrete words that participants could mentally represent with visual imagery. Less concrete words (e.g., worst, dug, pun, accident, etc.) were removed from 16-item lists, resulting in shorter 8-item lists. While our shorter lists frequently created false memories in participants during recall, they did not converge onto one specific critical lure to the extent that longer lists typically do; they activated other related words that were misremembered in addition to the critical lures. This illustrates the function of list length on the convergence of associative processing onto one critical lure. Thus, false memories may be underestimated during recall when using shorter lists if other related non-list words are not taken into account. If phonological processing is not of interest, the 3.2 protocol modification can be utilized to increase false memory rates using longer semantically-related lists.
This protocol utilizes immediate recall and final recognition tests. When both of these assessments are used in conjunction and separated by a delay (i.e., the 7-minute word search), instances of false memory that may not be captured by one task can be captured by the other. For instance, our immediate recall task captured phonological false memories that had decayed by final recognition, and our final recognition task captured semantic false memories that were successfully monitored, or possibly not activated, during immediate recall. The combined use of both tasks provides a more comprehensive examination of the mechanisms responsible for false memories, namely activation and monitoring. Depending on the variables of interest, this protocol can be easily adapted beyond the specific modifications provided here by varying presentation versions by a single variable and comparing recall and recognition performance across versions. It is our hope that this adaptability and construction-kit approach offered here proves particularly useful for research and classroom usage.
Divulgations
The authors have nothing to disclose.
Acknowledgements
We send special thanks Dr. Mary Ann Foley and Dr. Karen Zabrucky for collaborative work on research projects informing our methodology in this paper.
References
- Deese, J. On the prediction of occurrence of particular verbal intrusions in immediate recall. Journal of Experimental Psychology. 58 (1), 17-22 (1959).
- Roediger, H. L., McDermott, K. B. Creating false memories: Remembering words not presented in lists. Journal of Experimental Psychology: Learning, Memory, and Cognition. 21 (4), 803-814 (1995).
- Gallo, D. A. False memories and fantastic beliefs: 15 years of the DRM illusion. Memory & Cognition. 38 (7), 833-848 (2010).
- Lampinen, J. M., Neuschatz, J. S., Payne, D. G. Source attributions and false memories: A test of the demand characteristics account. Psychonomic Bulletin & Review. 6 (1), 130-135 (1999).
- Roediger, H. L., Balota, D. A., Watson, J. M., Roediger, H. L., Nairne, J. S., Neath, I., Surprenant, A. M. Spreading activation and arousal of false memories. The nature of remembering: Essays in honor of Robert G. Crowder. , 95-115 (2001).
- Roediger, H. L., Watson, J. M., McDermott, K. B., Gallo, D. A. Factors that determine false recall: A multiple regression analysis. Psychonomic Bulletin & Review. 8 (3), 385-407 (2001).
- Collins, A. M., Loftus, E. F. A spreading-activation theory of semantic processing. Psychological Review. 82 (6), 407-428 (1975).
- Buchanan, L., Brown, N. R., Cabeza, R., Maitson, C. False memories and semantic lexicon arrangement. Brain and Language. 68 (1-2), 172-177 (1999).
- Watson, J. M., Balota, D. A., Roediger, H. I. Creating false memories with hybrid lists of semantic and phonological associates: Over-additive false memories produced by converging associative networks. Journal of Memory And Language. 49 (1), 95-118 (2003).
- Robin, F. Imagination and false memories. Imagination, Cognition, and Personality. 30 (4), 407-424 (2011).
- Bays, R. B., Foley, M. A. Autobiographical memories and the DRM illusion: Investigating the content and process of lure activations. Applied Cognitive Psychology. 29 (5), 742-752 (2015).
- Foley, M. A. Imagery encoding and false recognition errors: Exploring boundary conditions of imagery’s enhancing effects. Memory. 20 (6), 700-716 (2012).
- Foley, M. A., Cowan, E., Schlemmer, E., Belser-Ehrlich, J. Acts of generating and their sources: Predicting the effects of imagery encoding on false recognition errors. Memory. 20 (4), 384-399 (2012).
- Oliver, M., Bays, R. B., Zabrucky, K. M. False memories and the DRM paradigm: Effects of imagery, list and test type. TheJournal of General Psychology. 143 (1), 33-48 (2016).
- Ballou, M. R., Sommers, M. S. Similar phenomena, different mechanisms: Semantic and phonological false memories are produced by independent mechanisms. Memory & cognition. 36 (8), 1450-1459 (2008).
- Garry, M., Manning, C. G., Loftus, E. F., Sherman, S. J. Imagination inflation: Imagining a childhood event inflates confidence that it occurred. Psychonomic Bulletin & Review. 3 (2), 208-214 (1996).
- Garry, M., Polascheck, D. L. L. Imagination and memory. Current Directions in Psychological Science. 9 (1), 6-10 (2000).
- Hyman, I. E., Pentland, J. The role mental imagery in the creation of false childhood memories. Journal of Memory and Language. 35 (2), 101-117 (1996).
- Bays, R. B., Zabrucky, K. M., Foley, M. A. Imagery induction processes differentially impact imagination inflation. Imagination, Cognition, and Personality. 35 (1), 5-25 (2015).
- Wade, K. A., Garry, M., Read, J. D., Lindsay, D. S. A picture is worth a thousand lies: Using false photographs to create false childhood memories. Psychonomic Bulletin & Review. 9 (3), 597-603 (2002).
- Foley, M. A., Wozniak, K. H., Gillum, A. Imagination and false memory inductions: investigating the role of process, content and source of imaginations. Applied Cognitive Psychology. 20 (9), 1119 (2006).
- McDermott, K. B., Watson, J. M. The rise and fall of false recall: The impact of presentation duration. Journal of Memory and Language. 45 (1), 160-176 (2001).
- Robin, F., Mahé, A. Effects of image and verbal generation on false memory. Imagination, Cognition and Personality. 35 (1), 26-46 (2015).

